Tcpdump Sophos
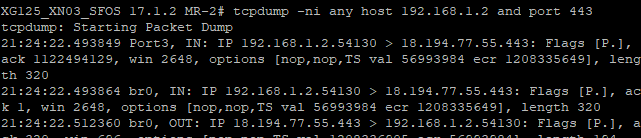
I analyze a tcpdump from a Sophos SG Firewall cluster, because we have Problems to send and receive Fax. Most of them cuttet. We only get or send a half Pages. In the dump file I see every Packet twice. Maybe its a mysterious of the Firewall Cluster? Has anyone seen this before? Sophos XG’s packet capture feature is a very useful tool when it comes troubleshooting connectivity issues. It provides a deeper level of information compared to looking at firewall log files. To be able to do basic troubleshooting on RED devices it would be fine to include CLI access and some basic commands like: tcpdump traceroute ping telnet (for Port checks). This would be fine, if something fails between remote location and central device. It would be nice to be able to prove functionality for other involved parties. Follow the steps below to create a packet capture on the Sophos XG Firewall and download it via the PSCP utility or from a web browser. Capture and download via the PSCP utility Starting a packet capture. Sign in to the CLI of the Sophos XG Firewall using PuTTY. Enter the following command: tcpdump filedump 'host.
Firewall software[edit]
| Firewall | License | Cost and usage limits | OS |
|---|---|---|---|
| Avast Internet Security | Proprietary | Paid | Microsoft Windows |
| Comodo Internet Security | Proprietary | Free | Windows 10/8.1/8/7/Vista x86/x64, XP x86 |
| Intego VirusBarrier | Proprietary | Paid | Mac OS X10.5 or later; on an Xserve |
| Kaspersky Internet Security | Proprietary | Paid / 30 day trial | Windows unknown versions x86/x64 |
| Lavasoft Personal Firewall | Proprietary | Paid | Windows unknown versions x86/x64 |
| Microsoft Forefront Threat Management Gateway | Proprietary | Discontinued | Windows unknown versions x64 |
| NetLimiter | Proprietary | Paid | Windows 10, 8, 7 x64 |
| Norton 360 | Proprietary | Paid | Windows unknown versions x86/x64 |
| Online Armor Personal Firewall | Proprietary | Discontinued | Windows unknown versions x86/x64 |
| Outpost Firewall Pro | Proprietary | Discontinued | Windows 10, 8, 7, Vista, XP x86/x64 |
| PC Tools Firewall Plus | Proprietary | Discontinued | Windows unknown versions x86/x64 |
| Sygate Personal Firewall | Proprietary | Discontinued | Windows unknown versions x86 |
| Windows Firewall | Proprietary | Included with Windows XP SP2 and later | Windows versions x86/x64 |
| ZoneAlarm | Proprietary | Free / Paid | Windows 10/8.1/8/7/Vista x86/x64, XP x86 |
| Netfilter/iptables | GPL | Free | Linux kernel module |
| nftables | GPL | Free | Linux kernel (>=3.13) module |
| Shorewall | GPL | Free | Linux-based appliance |
| PeerBlock | GPL | Free | Windows 8/8.1, 7, Vista x86/x64 |
| NPF | BSD | Free | NetBSD kernel module |
| PF | BSD | Free | *BSD kernel module |
| ipfirewall | BSD | Free | *BSD package |
| IPFilter | GPLv2 | Free | Package for multiple UNIX-like operating systems |
Firewall appliances[edit]
| Firewall | License | Cost | OS |
|---|---|---|---|
| Clavister | Proprietary | Included on all Clavister NGFWs | Proprietary operating system cOS Core |
| Check Point | Proprietary | Included on Check Point security gateways | Proprietary operating system Check Point IPSO and Gaia (Linux-based) |
| FortiGate | Proprietary | Included on all Fortigate devices | Proprietary, FortiOS, Based on the Linux kernel |
| Palo Alto Networks | Proprietary | Included on Palo Alto Networks firewalls | Proprietary, PAN-OS, Based on the Linux kernel |
| Sophos | Proprietary | Included on Sophos UTM | Linux-based appliance |
| Cisco ASA Firepower | Proprietary | Included on all CISCO ASA devices | Proprietary operating system. Based on the Linux kernel. |
| Cisco PIX | Proprietary | Included on all CISCO PIX devices | Proprietary operating system |
| Juniper SSG | Proprietary | Included on Netscreen security gateways | Proprietary operating system ScreenOS |
| Juniper SRX | Proprietary | Included on SRX security gateways | Proprietary operating system Junos |
| Sonicwall | Proprietary | Included on Dell appliance | Proprietary operating system SonicOS Based on the Linux kernel |
| Barracuda Firewall | Proprietary | Included Firewall Next Generation appliance | Windows-based appliance embedded firewall distribution |
| Cyberoam | Proprietary | Included Firewall Sophos appliance | Windows-based appliance embedded firewall distribution |
| D-Link | Proprietary | Included Firewall DFL | Windows-based appliance embedded firewall distribution |
| Endian Firewall | Proprietary | Free / Paid | Linux-based appliance |
| Forcepoint NGFW | Proprietary | Included on all Forcepoint NGFW devices | Proprietary operating system |
| OPNsense | Simplified BSD / FreeBSD License | Free / Paid | FreeBSD-based appliance firewall distribution |
| pfSense | Apache 2.0 / Proprietary (Plus) | Free / Paid | FreeBSD-based appliance firewall distribution |
| Zeroshell | GPL | Free / Paid | Linux/NanoBSD-based appliance firewall distribution |
| SmoothWall | GPL | Free / Paid | Linux-based appliance embedded firewall distribution |
| IPFire | GPL | Free (Donations welcomed) | Linux-based appliance embedded firewall distribution |
| WatchGuard | Proprietary | Included on all Firebox devices | Proprietary, Fireware OS, Based on the Linux kernel |
| WinGate | Proprietary | Free / Paid | Windows-based appliance embedded firewall distribution |
Firewall rule-set Appliance-UTM filtering features comparison[edit]
| Can Target: | Changing default policy to accept/reject (by issuing a single rule) | IP destination address(es) | IP source address(es) | TCP/UDP destination port(s) | TCP/UDP source port(s) | Ethernet MAC destination address | Ethernet MAC source address | Inbound firewall (ingress) | Outbound firewall (egress) |
|---|---|---|---|---|---|---|---|---|---|
| Trend Micro Internet Security | Yes | Yes | Yes | Yes | Yes | No | No | Yes | Yes |
| Vyatta | Yes | Yes | Yes | Yes | Yes | Yes | No | No | Yes |
| Windows XP Firewall | No | No | Yes | Partial[a] | No | No | No | Yes | No |
| Windows Vista Firewall | Yes | Yes | Yes | Yes | Yes | No | No | Yes | Yes |
| Windows 7 / Windows 2008 R2 Firewall | Yes | Yes | Yes | Yes | No | No | Yes | Yes | Yes |
| WinGate | Yes | Yes | Yes | Yes | Yes | No | No | No | Yes |
| Zeroshell | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| Zorp | Yes | Yes | Yes | Yes | Yes | Yes | No | No | No |
| pfSense | Yes | Yes | Yes | Yes | Yes | No | No | Yes | Yes |
| IPFire | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
- Notes
- ^can target only single destination TCP/UDP port per rule, not port ranges.
Firewall rule-set advanced features comparison[edit]
| Can: | work at OSI Layer 4 (stateful firewall) | work at OSI Layer 7 (application inspection) | Change TTL? (Transparent to traceroute) | Configure REJECT-with answer | DMZ (de-militarized zone) | Filter according to time of day (quota) | Redirect TCP/UDP ports (port forwarding) | Redirect IP addresses (forwarding) | Filter according to User Authorization | Traffic rate-limit / QoS | Tarpit | Log |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Sidewinder | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes | Yes |
| WinGate | Yes | Yes | Yes | No | Yes | Yes | Yes | No | Yes | Yes | No | Yes |
| Zeroshell | Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Yes |
| OPNsense | Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Yes |
| pfSense | Yes | Yes | No | Yes | Yes | Yes | Yes | Yes | Yes | Yes | No | Yes |
| IPFire | Yes | Yes | ? | No | Yes | Yes | Yes | Yes | ? | Yes | No | Yes |
| Features: | Configuration: GUI, text or both modes? | Remote Access: Web (HTTP), Telnet, SSH, RDP, Serial COM RS232, ... | Change rules without requiring restart? | Ability to centrally manage all firewalls together |
|---|---|---|---|---|
| WinGate | GUI | Proprietary user interface | Yes | N/A |
| ClearOS | both | RS232, SSH, WebConfig, | Yes | Yes with ClearDNS |
| Zeroshell | GUI | SSH, Web (HTTPS), RS232 | Yes | No |
| OPNsense | both | SSH, Web (HTTP/HTTPS), RS232 | Yes | No |
| pfSense | both | SSH, Web (HTTP/HTTPS), RS232 | Yes | No |
| IPFire | both | SSH, Web (HTTPS), RS232 | Yes | No |
Firewall's other features comparison[edit]
| Features: | Modularity: supports third-party modules to extend functionality? | IPS : Intrusion prevention system | Open-Source License? | supports IPv6? | Class: Home / Professional | Operating Systems on which it runs? |
|---|---|---|---|---|---|---|
| Vyatta | Yes | Yes | Yes | Yes | Professional | Vyatta OS (built on Debian) |
| WinGate | Yes[a] | ? | No | No | Professional | Windows 2000, Windows XP, Windows 2003, Windows Vista, Windows 2008. 32bit and 64bit. |
| OPNsense | Yes | Yes, with Snort and Suricata (modules) | Yes | Yes | Both | FreeBSD/NanoBSD-based appliance |
| pfSense | Yes | Yes, with Snort and Suricata (modules) | Yes | Yes | Both | FreeBSD/NanoBSD-based appliance |
| IPFire | Yes | Yes, with Suricata | Yes | Yes (manual setup needed) | Both | Linux (based on Linux From Scratch) |
- Notes
- ^WinGate 6.x supports 3rd party modules for data scanning only (e.g. antivirus and content filtering).
Non-Firewall extra features comparison[edit]
These are not strictly firewall features, but are sometimes bundled with firewall software or appliance. Features are also marked 'yes' if an external module can be installed that meets the criteria.
| Can: | NAT[a] | NAT64, NPTv6 | Intrusion Detection System (IDS)[b] | Virtual Private Network (VPN)[c] | Antivirus (AV) | Packet capture | Profile selection[d] |
|---|---|---|---|---|---|---|---|
| Vyatta | Yes (three NAT types) | ? | Yes (integrated Snort) | Yes (IPsec and OpenVPN) | Yes (with clamav, Sophos Antivirus (optional)) | Yes (with wireshark or tcpdump) | ? |
| WinGate | Yes | ? | Yes (with NetPatrol) | Yes (proprietary) | Yes (Kaspersky Labs) | Yes (filtered capturing to pcap format) | No |
| OPNsense | Yes | Yes (NPt) | Yes (integrated Suricata) | Yes (WireGuard, OpenVPN, IPsec, L2TP, IKEv2, Tinc, PPTP) | Yes (with squid and clamav) | Yes (tcpdump) | No |
| pfSense | Yes | Yes (NPt) | Yes (with Snort) | Yes (OpenVPN, IPsec, L2TP, IKEv2, Tinc, PPTP) | Yes (with squid and clamav) | Yes (tcpdump) | No |
| IPFire | Yes | ? | Yes (with Snort) | Yes (OpenVPN, IPsec, IKEv2) | Yes (with squid and clamav) | Yes (tcpdump) | No |
- Notes
- ^static, dynamic w/o ports, PAT
- ^monitors for malicious activity or policy violations
- ^types include: PPTP, L2TP, MPLS, IPsec, SSL
- ^store sets of firewall settings to switch between
See also[edit]
References[edit]
Sophos Connect client is VPN software that runs on Microsoft Windows 7 SP2 and later, and Mac OS 10.12 and later. It establishes highly secure, encrypted VPN tunnels for off-site employees.
You can download the Sophos Connect client and Sophos Connect Admin by clicking Download on the Sophos Connect client page. You can check if the pattern for the Sophos Connect client has been downloaded from Backup & Firmware > Pattern updates.
- Enable the Sophos Connect client, specify VPN settings and add users on the Sophos Connect client page.
- Add a firewall rule so that the Sophos Connect clients can access the configured LAN networks. For information on how to add a firewall rule, see Add a firewall rule. If you want to allow LAN and VPN traffic in both directions, add both LAN and VPN to the source and destination zones. If you want to allow specific traffic for each direction, you need to create separate rules.
To export a connection, enable the Sophos Connect client and click Export connection.
The remote users import the connection file and establish a connection using the Sophos Connect client. See Sophos Connect Help for more details.
To revert to factory settings, click Reset.
General settings
Sophos Tcpdump Port
Authentication to use for the connection.Preshared key: Authenticates endpoints using the secret known to both endpoints.
Digital certificate: Authenticates endpoints by exchanging certificates (either self-signed or issued by a certificate authority).
Client information
Sophos Tcpdump Filedump
Advanced settings
Sophos Tcpdump File
- Disconnect when tunnel is idle
- Disconnects idle clients from the session after the specified time.
- Idle session time interval
- Time, in seconds, after which idle clients will be disconnected.
